In the world of cyber-attacks, another malevolent malware PowerWare ransomware, a Trojan ransomware has made its way to the systems. It uses a complicated file-less operation method to encipher the data. This makes its detection and removal ill-timed and difficult. Most of the computer systems run Windows OS that is a native framework, PowerShell. PowerWare ransomwarecash withholds rights from the PowerShell to start its manipulation of data.
Since few months the structure of PowerWare ransomware has been changed into a more useful one for gaining the benefits. It launches a series of infections as abnormal threats that are very complex to handle.
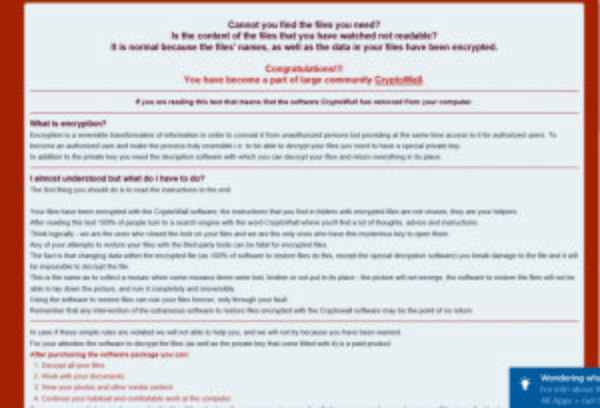
How does it attack?
In technical terms it adopts file-less method to encode the data through numerous security apps. It attacks in the same way as Petya ransomware does. The difference comes in the content of email only. For instance, the users receives a word file in an email and is required to go through it considering its importance. The user then directly opens the file from email without bothering to download it. In doing so, the user is asked to enable macros. While the users does it, command center pops up and the destructive script is added. The scripts causes the complete takeover of the background by the evil-intentioned PowerWare ransom. It enciphers the files, but if it begins to read the actual data in the files, it might blackmail the user in a more unappropriated manner. After doing so, it demands $500 to reveal the decryption key and threatens to double the amount if the payment is not made by the given deadline.
What to do
Just like any other malware PowerWare ransomware can be detected, prevented and washed out of the system. Apart from the traditional AV and firewall, you need to make use of other solutions too:
- The harmful malware might be hiding in the cache memory and when the right time comes it may disable your browser. Keep changing your browsers. Use Firefox, Safari and Chrome alternatively.
- Install and upgrade a security software on other computer and then use removable media to transfer it to the victim computer.
- Enable safe mode of the windows OS. Reboot your computer whenever necessary.
- Disable the proxy servers from the browsers. The PowerWare ransomware may be playing games behind the screen with the proxy settings.
- HIDS and FIM agents work best to help your computer remain secure from the encrypting scripts. They alert you right on time, make essential configurations and shuts down the encoding process before the malware begins to encrypt.
The vitriolic PowerWare Ransomware is attacking a huge number of health care institutes. It is taking undue advantage of the lax security practice of the healthcare centers. It is setting the security of the future organizations on a greater risk of cyber-attacks. Do not pay heed to cyber extortionists. Start working on the prevention ideas from today and defend your systems.
How to remove Powerware Ransomware
If you are infected with Powerware Ransomware. Them simply follow the following procedure to make your PC clean from all type of trojan and other malware infections.
- Scan your computer with a Good and effective Antimalware Software like Hitman Pro and Malwarebytes. You can scan with multiple malware cleaner software to make sure that there is no traces left behind.
- Scan computer with a good antivirus software or with an online virus scanner.
- Try to recover the data.